Architecture
Architecture Diagram
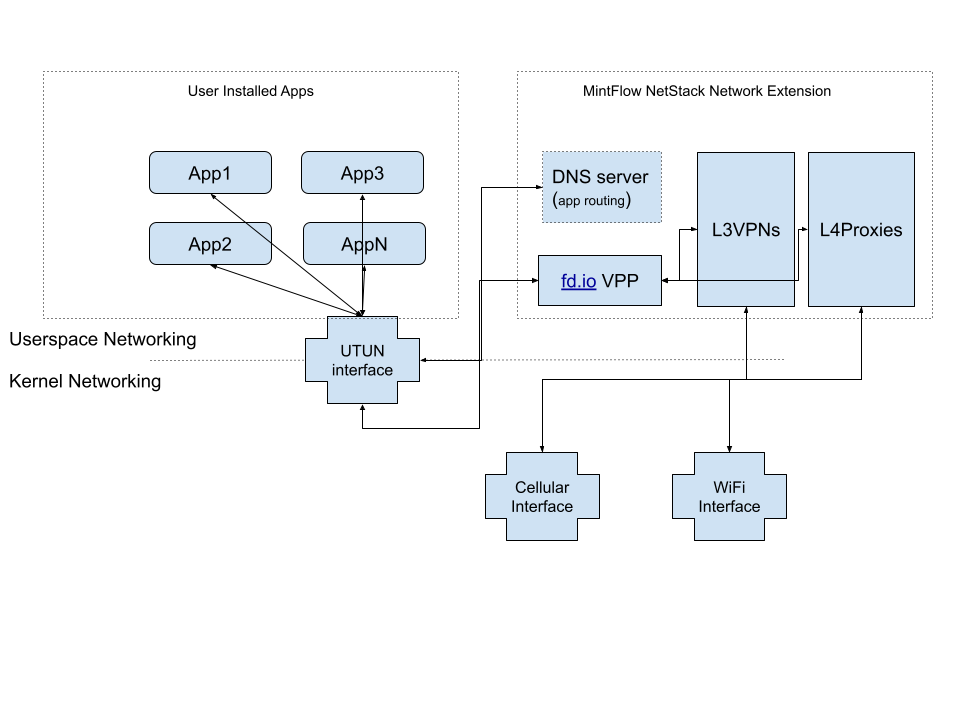
Here's a brief diagram showing the MintFlow NetStack Network Extension architecture and how user-installed apps leverage it to improve privacy and unlock limited content.
Important Concepts
UTUN Interface
When the Network Extension runs on iOS, Apple allocates a UTUN interface that can be configured to route packets by IP address using LPM (longest prefix match) to the UTUN interface. These packets are then received by the Network Extension's process for handling.
By default, MintFlow NetStack will configure to route all App's traffic to UTUN interface, to enable user to do advanced routing and filtering.
MintFlow NetStack settings include an 'Exclude LAN Networks' toggle that excludes the following well-known LAN network ranges from entering the UTUN interface:
- 10.0.0.0/8
- 172.16.0.0/16
- 192.168.0.0/16
Important: If your L3VPN provides access to remote networks using the same LAN ranges listed above, you must not enable this option. Otherwise, you won't be able to reach the networks that your L3VPN provides.
fd.io VPP
This is the core differentiator of MintFlow NetStack. Unlike other VPN apps that use the LwIP stack, we've ported fd.io VPP for the Apple platform to achieve a WireGuard implementation written in pure C for optimal performance. We also leverage VPP's advanced host stack to perform TCP/IP session reconstruction and dispatch sessions to local internet or proxies.
DNS Server
When users enable app routing in MintFlow NetStack, it starts an internal DNS server that handles domain queries initiated by iOS or user-installed apps.
The app routing rules that match domain sets determine which upstream DNS server the internal DNS server will query. The results are then populated to fd.io VPP to route the packets/sessions to L3VPN/L4Proxy/Direct/Drop/Reject virtual interfaces.
HTTP Engine
When users enable app routing in MintFlow NetStack, you can optional enable HTTP engine which can capture and rewrite HTTP/HTTPS traffic.
L3VPNs&L4Proxies
For L3VPN protocols, we implement them natively in fd.io VPP using the C language, allowing us to use VPP's vectorized packet processing for maximum performance.
For L4Proxy protocols, we implement them in Rust, a memory-safe language that increases stability while maintaining low runtime overhead. We use an internal high-performance protocol to proxy packets in and out of fd.io reconstructed sessions.